Introducing lynk-mcp: MCP for Talking to Your Software Supply Chain
Jan 24, 2026
Interlynk
What if managing your software supply chain security was as simple as asking a question?
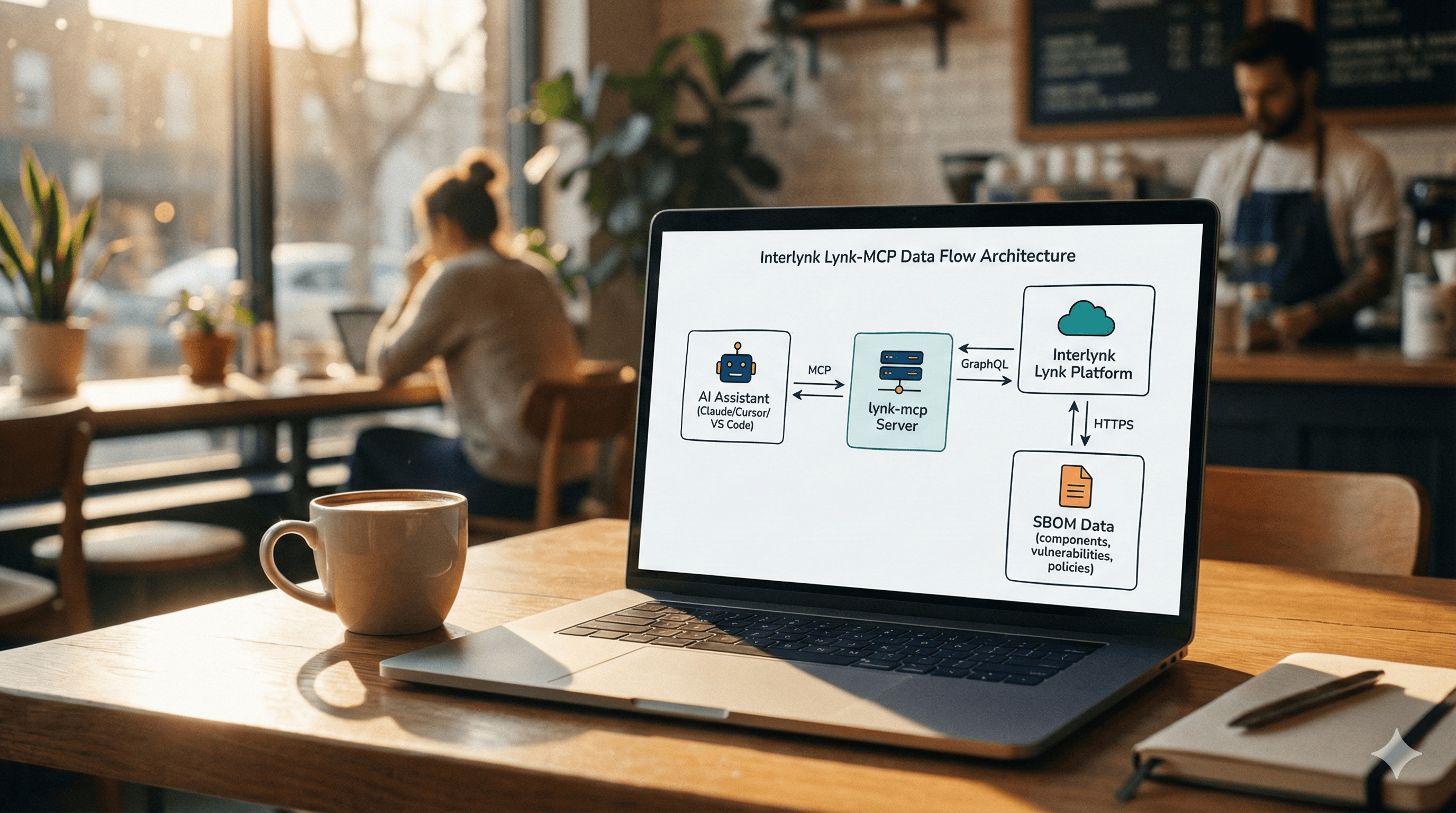
Today, we're thrilled to announce lynk-mcp - an open-source Model Context Protocol (MCP) server - a new standard for securely connecting AI assistants to local tools and data - that connects your AI assistant directly to the Interlynk platform.
For the first time, developers, security teams, and compliance officers can query SBOMs, vulnerabilities, and policies using plain English through Claude, Cursor, VS Code, and other AI-powered tools.
The Problem: Supply Chain Security Data Is Trapped
Software supply chain security has never been more critical. With regulations like the Executive Order on Improving the Nation's Cybersecurity and the EU Cyber Resilience Act, organizations must maintain comprehensive visibility into their software components, vulnerabilities, and compliance posture.
But here's the challenge: the data exists, but accessing it is painful.
Security teams spend hours navigating dashboards, writing queries, and cross-referencing multiple tools just to answer basic questions. Developers context-switch between their IDE and security platforms. Compliance officers manually compile reports from disparate sources.
The result? Security insights arrive too late, vulnerabilities slip through, and teams burn out on toil.

The Solution: AI-Native Supply Chain Security
lynk-mcp transforms how teams interact with supply chain security data. By implementing the Model Context Protocol, it creates a bridge between your favorite AI assistants and the Interlynk Lynk platform.
Instead of learning query syntax or navigating complex UIs, you simply ask:
And get an immediate, contextual answer.
How It Works
lynk-mcp exposes 24 specialized tools that cover the full spectrum of supply chain security operations:
Category | Capabilities |
|---|---|
Organization & Products | View metrics, browse products, explore environments |
Versions & Components | Track releases, analyze dependencies, compare versions |
Vulnerabilities | Search CVEs, filter by severity/KEV/EPSS, track VEX status |
Policies & Compliance | Evaluate security policies, track violations, monitor licenses |
The AI understands context, chains multiple operations together, and presents results in human-readable summaries - all within your existing workflow.
Real-World Use Cases
For Security Teams: Rapid Vulnerability Triage
Stop drowning in CVE feeds. With lynk-mcp, security analysts can instantly surface what matters:
The impact: Hours of triage reduced to seconds. Security teams can focus on remediation instead of research.
For Developers: Security Without Context Switching
Integrate security awareness directly into your development environment. Query your supply chain without leaving VS Code or Cursor:
The impact: Developers get security context at the moment they need it, embedded in their natural workflow.
For Compliance Officers: Effortless Audit Preparation
Generate compliance evidence and track policy adherence conversationally:
The impact: Audit preparation that took days now happens in minutes.
Enterprise Ready Features
Drift Analysis Between Versions
Understand exactly what changed between releases - new components, removed dependencies, emerging vulnerabilities, and resolved issues:
VEX Integration
Full support for Vulnerability Exploitability Exchange (VEX) data, so you can see not just what's vulnerable, but what actually affects you:
Affected – Vulnerability is exploitable in your context
Not Affected – Mitigating factors prevent exploitation
Fixed – Remediation has been applied
Under Investigation – Analysis in progress
KEV & EPSS Intelligence
Prioritize based on real-world threat intelligence:
KEV (Known Exploited Vulnerabilities) – CISA's catalog of actively exploited vulnerabilities
EPSS (Exploit Prediction Scoring System) – Probability of exploitation in the wild
Security-First Design
We built lynk-mcp with enterprise security requirements in mind:
Secure Credential Storage – API tokens stored in your system's native keychain (macOS Keychain, Windows Credential Manager, Linux secret service)
No Token Exposure – Credentials never appear in logs, error messages, or configuration files
HTTPS Only – All communication encrypted in transit
Organization-Scoped Access – Respects your Lynk platform's access controls
Getting Started
Installation
macOS/Linux (Homebrew)
Docker
Go Install
Configuration
Interactive setup - stores token securely in system keychain
Verify connection
Connect to Your AI Assistant
Claude Desktop – Add to your claude_desktop_config.json:
VS Code – Add to your settings.json:
That's it. Start asking questions.
Join the Community
lynk-mcp is open source under the Apache 2.0 license. We believe supply chain security tools should be transparent and community-driven.
Star us on GitHub: github.com/interlynk-io/lynk-mcp
Issues & Feature Requests: GitHub Issues
Community Slack: Join the conversation with security practitioners worldwide
Documentation: Comprehensive guides and API reference
What's Next
This is just the beginning. Our roadmap includes:
Additional AI Platforms – Support for more MCP-compatible assistants
Custom Prompts – Pre-built prompt templates for common workflows
Automated Alerts – Proactive notifications through AI assistants
Extended Analytics – Trend analysis and predictive insights
CI/CD Integration – Query your supply chain directly from pipelines
We're building the future of AI-native supply chain security, and we want you to be part of it.
Try It Today
The software supply chain doesn't have to be a black box. With lynk-mcp, your entire SBOM portfolio is just a question away.
Then open your AI assistant and ask: What does my software supply chain look like?
You might be surprised by the answer - and how easy it was to get it.
